The Feynman (Robot) Years
This is a continued post about my robots as I prepare to archive and rebuild ScottsBots.Com.
Feynman MK1 – 2002
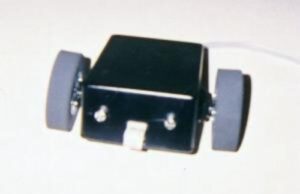
The “Feynman” name for my robots actually comes from the names of the computers in my house, this computer housed in wood below was called Feynman, and I happened to turn it into a robot.

This robot came equipped with a robot arm, sonar, a compass, and a webcam. The chassis was made from plywood and PVC. The motors were Black & Decker cordless drills. I powered the drills via speed controls from robot control cars. It had speakers and could “talk” using primitive text to speech. It was still powered via 110 VAC.
The computer itself was an AMD K6-2 500MHz, running Windows 2000 and Visual Basic 6. I programmed and tested it using VNC. I used a Basic Stamp 2 to get sensor readings from the sonar, compass and infrared sensors. I used the Scott Edwards Mini-SSC to control PWM channels on the speed controller connected to the drill motors.
Computer Vision Tinkering

From the image above, I also started to tinker with computer vision. This was a simple VB6 thresholding program, where i looped through all the pixels and if they were below a certain number I changed them to zero (black) and if they were above it, I changed the pixel to 255 (white).
Feynman MK3 – 2003

This version contained a lot of upgrades. I still had a plywood base but I used 80/20 Aluminum Extrusion for the chassis and I used 2 33AH Batteries for power. I upgraded the drive motors to use two windshield wiper motors from an F-150. I upgraded the speed controls to two Victor 883 from IFI Robotics @$150 each. I upgraded the webcams to Two Pyro 1394 Firewire webcams.
The computer changed to a lower powered version. VIA EPIA M10000 Mini-ITX with 259 MB of ram and a 20GB HDD. It had Wi-Fi and all the software to program and run it was 100% Java.

This is a picture of the base of the robot. The drive system used coupling nuts connected directly to the shaft of the wiper motors and the wheels. This wasn’t very efficient and the motors themselves didn’t prove to be that reliable. Another thing I didn’t do well with this design was account for the spacing of the caster wheels. They were a little above the drive wheel and movement of this robot was a little jarring as it would rock back and forth when starting and stopping. This rocking eventually led a really difficult time doing computer vision with the two cameras, ultimately i needed a better solution.
Feynman MK5 – 2004
This was the robot I used for my book, The Definitive Guide to Building Java Robots.

This design and software to run it is outlined completely in the book. Additional upgrades include PVC from McMaster Carr. Two new NPC-41250 Motors from National Power Chair. 3 SRF-4 Devantech Sonar Sensors. I also removed the front caster made it a little backwards heavy so it rested on the batteries. This created a much more stable platform for moving around doing navigation.
Feynman MK6 – 2005
Once I wrote the book I started getting invited to speak at local user groups and conferences about Java and Robots.

I created a switch so that I could remote control the robot as I would drive it places. This is the robot at some location in town, it could even be a conference. This robot is mostly the same as Feynman 5, just a little taller with a single webcam.
I think this was the first version of my robot I took to CodeMash. as speaker.
Feynman MK7 – 2006
This is the final version of the robot.

Most of this robot remains unchanged to this day. I removed and upgraded the computer a few times, eventually switching to a Raspberry Pi, but ultimately the robot proved too difficult to transport. It weighted about 200 pounds and required 2-3 people to load into the truck to transport to conferences and meet-ups. Currently this robot sits in the garage unused. 🙁
The Feynman (Robot) Years Read More »